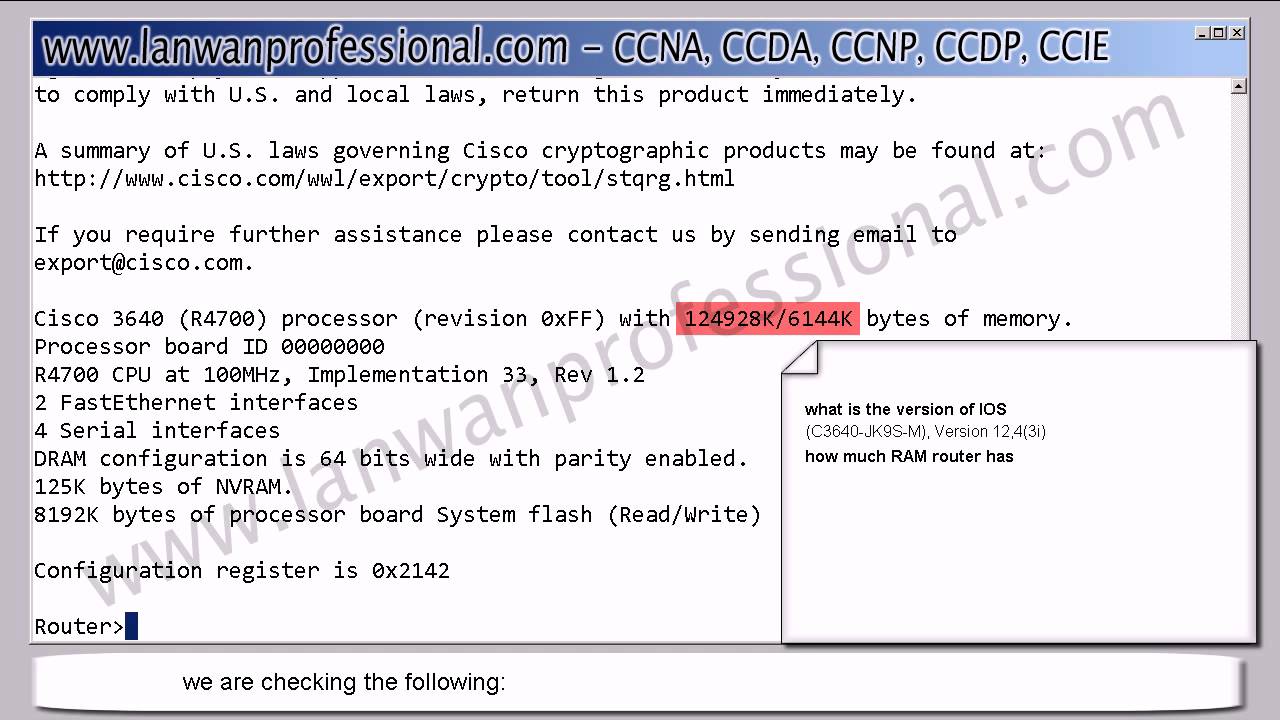
IOS is the main code that the routers run, consider that to be like the operating system on your computer (ie. Windows xp or whatever). Cisco IOS Software, C2900 Software (C2900-UNIVERSALK9-M), Version 15.1(4)M4, RELEASE SOFTWARE (fc1) And Justin showed you how to get the current version. Download Cisco IOS for GNS3. All versions are tested and are working with the latest version of GNS3. Happy GNS3'ing. When autocomplete results are available use up and down arrows to review and enter to select.
This is the Cisco response to research performed by Mr. Philipp Schmidt and Mr. Jens Steube from the Hashcat Project on the weakness of Type 4 passwords on Cisco IOS and Cisco IOS XE devices. Mr. Schmidt and Mr. Steube reported this issue to the Cisco PSIRT on March 12, 2013.Cisco would like to thank Mr. Schmidt and Mr. Steube for sharing their research with Cisco and working toward a coordinated disclosure of this issue.
This video talks about the Cisco IOS versions, LAN Lite, LAN Base, IP Base and IP Services.
This Cisco Security Response is available at https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130318-type4- The FXOS versions with (EoL) appended have reached their end of life (EoL), or end of support. (Originally-supported Cisco IOS Version 12.2(33)SXJ1 has a.
- As of 2018, two versions of iOS were never released. IPhone OS 1.2, which after the first beta was replaced by a 2.0 version number; the second beta was named 2.0 beta 2 instead of 1.2 beta 2. The other was iOS 4.2, replaced with 4.2.1 due to a Wi-Fi bug in 4.2 beta 3, causing Apple to release 2 golden masters (4.2 GM and 4.2.1 GM).
Additional Information
A limited number of Cisco IOS and Cisco IOS XE releases basedon the Cisco IOS 15 code base include support for a new algorithm tohash user-provided plaintext passwords. This algorithm is called Type 4, and a password hashed using this algorithm is referred to as a Type 4 password.The Type 4 algorithm was designed to be a stronger alternative to theexisting Type 5 and Type 7 algorithms to increase the resiliency ofpasswords used for the enable secretpassword and usernameusernamesecretpassword commands against brute-force attacks.
The design called for using Password-Based Key Derivation Functionversion 2 (PBKDF2), as described in RFC 2898 section 5.2, with thefollowing input values:- Hash algorithm = SHA-256
- Password = the user-provided plaintext password
- Salt = 80 bits (generated by calling a cryptographically secure random number generator)
- Iteration count = 1,000 (one thousand)
Due to an implementation issue, the Type 4 password algorithm does not use PBKDF2 and does notuse a salt, but instead performs a single iteration of SHA-256 over theuser-provided plaintext password. This approach causes a Type 4password to be less resilient to brute-force attacks than a Type 5password of equivalent complexity.
The following issues were also introduced because of the implementation of Type 4 passwords:
- A device running a Cisco IOS or IOS XE release with support for Type 4 passwords lost the capability to create a Type 5 password from a user-provided plaintext password
- Backward compatibility problems may arise when downgrading from a device running a Cisco IOS or IOS XE release with Type 4 password support and Type 4 passwords configured to a Cisco IOS or Cisco IOS XE release that does not support Type 4 passwords. Depending on the specific device configuration, the administrator may not be able to log in to the device or to change into privileged EXEC mode, requiring a password recovery process to be performed.
All the preceding issues apply only to devices running Cisco IOSor Cisco IOS XE releases with support for Type 4 passwords, and only tothe 'enable secret <password>' and 'username <username>secret <password>' commands. No other Cisco IOS or IOS XEfeatures use this algorithm to hash passwords or keys. For example,these issues do not affect Open Shortest Path First (OSPF), BorderGateway Protocol (BGP), Routing Information Protocol (RIP), any otherrouting protocol keys, or pre-shared keys for IPsec.
These issues do not apply to devices running a Cisco IOS or Cisco IOS XE release without support for Type 4 passwords.
This issue is documented in Cisco Bug ID CSCue95644 (registered customers only).
Determining Whether a Cisco IOS or Cisco IOS XE Release Supports Type 4 Passwords
Administrators can use the following procedure to determine whetherthe Cisco IOS or Cisco IOS XE release running on a given device includessupport for Type 4 passwords:
1) Log in to the device and execute the show version | include IOS command:
If the version number starts with '15' proceed to the next step. Otherwise, the Cisco IOS or Cisco IOS XE release running on the device does not include support for Type 4 passwords.2) While logged in to the device as a privileged user, enter configuration mode and execute an enable secret ? command:
In the preceding example, the line '4 Specifies an SHA256 ENCRYPTED secret will follow' indicates the Cisco IOS or Cisco IOS XE release running on the device does supports Type 4 passwords.
In the preceding example, there is no '4 Specifies an SHA256 ENCRYPTED secret will follow' in the help output of the enable secret command. This output indicates the Cisco IOS or Cisco IOS XE release running on this device does not support Type 4 passwords.
Determining Whether a Device Has Any Type 4 Passwords Configured
A device running a Cisco IOS or Cisco IOS XE release with support forType 4 passwords may not actually have any Type 4 passwords in thedevice configuration. A device that was upgraded from a Cisco IOS orCisco IOS XE release without support for Type 4 passwords to a Cisco IOSor Cisco IOS XE release that does support Type 4 passwords may containan enable secret password command and zero or more username username secret password commands that have Type 5 passwords because they were configured before the upgrade.The following command can be used to determine whether any Type 4 passwords are present on the device configuration:
The following example shows a device without any Type 4 passwords configured:
The following example shows a device with Type 4passwords configured for both the 'enable secret <password>' andthe 'username <username> secret <password>' commands. The presence of a Type 4 password is indicated by the number 4 that immediately follows the secret keyword:
Behavior of a Cisco IOS or Cisco IOS XE Release with Support for Type 4 Passwords
A device running a Cisco IOS or Cisco IOS XE release with support for Type 4 passwords will exhibit the following behavior:1) Configuring an enable secretpassword or username username secret password command (with password being a plaintext password) will cause a Type 4 password to be generated:
Note: There is no way to supply a plaintext password as an argument to either the enable secret password or username username secretpassword and indicate that a Type 5 password should be generated. The only way to configure either an enable secret password or username
 username
username Cisco Ios Versions History
secret password with a Type 5 password is using the enable secret 5password or username username secret 5password commands, where password is a previously generated Type 5 password.2) Configuring an enable secret 5password or usernameusernamesecret 5
 password (where passwordis a previously generated Type 5 password) will result in a warning,but the password will be correctly parsed, added to the configuration,and fully functional. The generated warning can safely be ignored. Anexample follows:
password (where passwordis a previously generated Type 5 password) will result in a warning,but the password will be correctly parsed, added to the configuration,and fully functional. The generated warning can safely be ignored. Anexample follows:3) If the device was upgraded from a previous Cisco IOS or Cisco IOS XE release without support for Type 4 passwords, and the configuration included the commands enable secret 5password or usernameusernamesecret 5password, those Type 5 passwords will be parsed, added to the configuration, and fully functional. Thereis no automatic conversion of existing Type 5 passwords to Type 4passwords after upgrading a device to a Cisco IOS or Cisco IOS XErelease that has support for Type 4 passwords.
Replacing a Type 4 Password with a Type 5 Password
Customers running a Cisco IOS or Cisco IOS XE release with support forType 4 passwords and currently using Type 4 passwords on their deviceconfiguration may want to replace those Type 4 passwords with Type 5passwords. Reasons include the following:- Preparation for a device downgrade to a Cisco IOS or Cisco IOS XE release that does not support Type 4 passwords
- Compatibility with network management systems or other tools that cannot handle a device configuration that includes Type 4 passwords
- An organizational security policy that dictates the use of Type 5 passwords
- Concerns about the resiliency of Type 4 passwords versus Type 5 passwords against brute-force attacks
There are two options to generate a Type 5 password:
- Using another device running a Cisco IOS or Cisco IOS XE release without Type 4 support
- Using the openssl command-line tool (part of the OpenSSL Project)
Using Another Device to Generate a Type 5 Password
1) Either the enable secretpassword or the usernameusernamesecret passwordcommand can be used to generate a Type 5 password from a plaintextpassword. The administrator must log in to the device using credentialsthat allow the administrator to go into configuration mode and executethe chosen command. The following example shows the usernameusernamesecret password command and the string Th1z#1s+53kri7 as the plaintext password:2) Copy the resulting Type 5 password (which is $1$M/wf$iqBnv/g3GuVUsCpWcDFS20 in the preceding example).
Using the openssl Tool to Generate a Type 5 Password
1) The openssl tool can generate a Type 5 password when using a specific set of command-line arguments, as follows:Administrators must replace the string PLAINTEXT_PASSWORD with the appropriate plaintext password. The following example uses the string Th1z#1s+53kri7 as the plaintext password:
2) Copy the resulting Type 5 password (which is $1$dxVt$FSJmj1O6JUZdbUjxZkIuD. in the preceding example).
Note: Depending on the characters in the plaintext password, you may need to enclose it between quotes.
Copying the Type 5 Password to the Targeted Device
Paste the previously generated Type 5 password into the appropriate command, either enable secret 5password or usernameusernamesecret 5Cisco Ios Release History
password. Remember to specify the type of encryption by adding the numberCisco Ios Versions Catalyst 9500
5 after the secret keyword in both commands. Otherwise, the provided password will be interpreted as a plaintext password.The following example uses the Type 5 password generated on another device as the enable secret password, and the Type 5 password generated by openssl becomes the user password for the user named demo:
Notes
- A deprecation warning will be generated when using a Type 5 password for either the enable secret 5 command or the usernameusernamesecret 5password command. This warning can be safely ignored.
- If the deprecation warning for either the enable secret 5 command or the usernameusernamesecret 5password command does not occur, the device is not interpreting the provided password as a Type 5 password. Make sure the number 5 is included after the secret keyword in either command.
The Future of Type 4 Passwords on Cisco IOS and Cisco IOS XE
Because of the issues discussed in this Security Response, Cisco istaking the following actions for future Cisco IOS and Cisco IOS XEreleases:- Type 4 passwords will be deprecated: Future Cisco IOS and Cisco IOS XE releases will not generate Type 4 passwords. However, to maintain backward compatibility, existing Type 4 passwords will be parsed and accepted. Customers will need to manually remove the existing Type 4 passwords from their configuration.
- The enable secretpassword and usernameusernamesecret password commands will revert to their original behavior: Both commands, when provided with a plaintext password, will generate a Type 5 password. This will be the same behavior as before the introduction of Type 4 passwords. This step is being taken to preserve backward compatibility.
- Type 5 passwords will not be deprecated: This will be done to preserve backward compatibility. The deprecation warning for Type 5 passwords will be removed.
- A new password type will be introduced: This new password type will implement the original design intended for Type 4 passwords, which is PBKDF2 with SHA-256, an 80-bit salt, and 1,000 iterations. The exact type is yet to be determined.
- New command-line interface commands will be introduced: The new commands will allow Cisco customers to configure the new password type for both enable secretpassword and usernameusernamesecret password. This will allow Cisco customers to gradually migrate to the new password type, while allowing them to use the existing syntax to preserve backward compatibility. The exact syntax for the new commands is yet to be determined.
Affected Cisco IOS and Cisco IOS XE Releases
The following table lists the Cisco IOS and Cisco IOS XE releases affected by this issue as of March 22, 2013:| Affected 15.0-Based Cisco IOS and Cisco IOS XE Releases | Affected Cisco IOS and Cisco IOS XE Versions |
|---|---|
| 15.0EA | 15.0(2)EA |
| 15.0EB | 15.0(2)EB |
| 15.0EC | 15.0(2)EC |
| 15.0ED | 15.0(2)ED |
| 15.0EX | 15.0(1)EX, 15.0(1)EX1, 15.0(2)EX, 15.0(2)EX1 |
| 15.0EY | 15.0(2)EY, 15.0(2)EY1 |
| 15.0EZ | 15.0(1)EZ, 15.0(2)EZ |
| 15.0MR | 15.0(1)MR, 15.0(2)MR |
| 15.0MRA | 15.0(1)MRA |
| 15.0S | 15.0(1)S, 15.0(1)S1, 15.0(1)S10, 15.0(1)S2, 15.0(1)S3a, 15.0(1)S4, 15.0(1)S4a, 15.0(1)S5, 15.0(1)S6 |
| 15.0SE | 15.0(2)SE, 15.0(2)SE1, 15.0(2)SE2, 15.0(2)SE3, 15.0(2)SE4 |
| Affected 15.1-Based Cisco IOS and Cisco IOS XE Releases | Affected Cisco IOS and Cisco IOS XE Versions |
| 15.1EY | 15.1(2)EY, 15.1(2)EY1, 15.1(2)EY1a, 15.1(2)EY2, 15.1(2)EY2a, 15.1(2)EY3, 15.1(2)EY4 |
| 15.1GC | 15.1(4)GC, 15.1(4)GC1 |
| 15.1M | 15.1(4)M10, 15.1(4)M4, 15.1(4)M5, 15.1(4)M6, 15.1(4)M7, 15.1(4)M8 |
| 15.1MR | 15.1(1)MR, 15.1(1)MR1, 15.1(1)MR2, 15.1(1)MR3, 15.1(1)MR4, 15.1(1)MR5, 15.1(1)MR6, 15.1(3)MR |
| 15.1MRA | 15.1(3)MRA, 15.1(3)MRA1 |
| 15.1S | 15.1(1)S, 15.1(1)S1, 15.1(1)S2, 15.1(2)S, 15.1(2)S1, 15.1(2)S2, 15.1(3)S, 15.1(3)S0a, 15.1(3)S1, 15.1(3)S2, 15.1(3)S3, 15.1(3)S4, 15.1(3)S5, 15.1(3)S6 |
| 15.1SA | 15.1(1)SA, 15.1(1)SA1, 15.1(1)SA2 |
| 15.1SG | 15.1(1)SG, 15.1(1)SG1, 15.1(1)SG2, 15.1(2)SG, 15.1(2)SG1 |
| 15.1SNG | 15.1(2)SNG |
| 15.1SNH | 15.1(2)SNH, 15.1(2)SNH1 |
| 15.1SNI | 15.1(2)SNI |
| 15.1SVA | 15.1(3)SVA |
| 15.1SVB | 15.1(3)SVB, 15.1(3)SVB1 |
| 15.1SVC | 15.1(3)SVC |
| 15.1XB | 15.1(4)XB8, 15.1(4)XB8a |
| Affected 15.2-Based Cisco IOS and Cisco IOS XE Releases | Affected Cisco IOS and Cisco IOS XE Versions |
| 15.2E | 15.2(1)E, 15.2(2)E |
| 15.2GC | 15.2(2)GC, 15.2(3)GC, 15.2(3)GC1 |
| 15.2GCA | 15.2(3)GCA, 15.2(3r)GCA |
| 15.2JA | 15.2(4)JA |
| 15.2M | 15.2(4)M, 15.2(4)M1, 15.2(4)M10, 15.2(4)M2, 15.2(4)M3, 15.2(4)M4, 15.2(4)M5, 15.2(4)M6, 15.2(4)M7, 15.2(4)M8, 15.2(4)M9 |
| 15.2S | 15.2(1)S, 15.2(1)S0a, 15.2(1)S1, 15.2(1)S2, 15.2(2)S, 15.2(2)S0a, 15.2(2)S0b, 15.2(2)S0c, 15.2(2)S0d, 15.2(2)S1, 15.2(2)S2, 15.2(4)S, 15.2(4)S0c, 15.2(4)S0xb, 15.2(4)S1, 15.2(4)S1c, 15.2(4)S2, 15.2(4)S2t, 15.2(4)S3, 15.2(4)S4, 15.2(4)S5, 15.2(4)S6 |
| 15.2SA | 15.2(1)SA, 15.2(2)SA |
| 15.2SB | 15.2(1)SB, 15.2(1)SB1, 15.2(1)SB2, 15.2(1)SB3, 15.2(1)SB4 |
| 15.2SC | 15.2(1)SC, 15.2(1)SC1 |
| 15.2SNG | 15.2(2)SNG |
| 15.2SNH | 15.2(2)SNH, 15.2(2)SNH1 |
| 15.2SNI | 15.2(2)SNI |
| 15.2T | 15.2(2)T1, 15.2(2)T2, 15.2(2)T3, 15.2(2)T4, 15.2(3)T1, 15.2(3)T2, 15.2(3)T3, 15.2(3)T4 |
| 15.2XB | 15.2(4)XB10, 15.2(4)XB11 |
| Affected 15.3-Based Cisco IOS and Cisco IOS XE Releases | Affected Cisco IOS and Cisco IOS XE Versions |
| 15.3T | 15.3(1)T, 15.3(1)T1, 15.3(1)T2, 15.3(1)T3, 15.3(1)T4, 15.3(2)T, 15.3(2)T1, 15.3(2)T2 |
| 15.3S | 15.3(1)S, 15.3(2)S, 15.3(3)S |
| Affected 15.4-Based Cisco IOS and Cisco IOS XE Releases | Affected Cisco IOS and Cisco IOS XE Versions |
| 15.4S | 15.4(1)S |
Cisco Security Procedures
Complete information on reporting security vulnerabilities in Ciscoproducts, obtaining assistance with security incidents, and registering toreceive security information from Cisco, is available on Cisco's worldwidewebsite athttp://www.cisco.com/web/about/security/psirt/security_vulnerability_policy.html.This includes instructions for press inquiries regarding Cisco securitynotices. All Cisco security advisories are available athttp://www.cisco.com/go/psirt.